Abusing Resource-Based Constrained Delegation (RBCD) using Linux
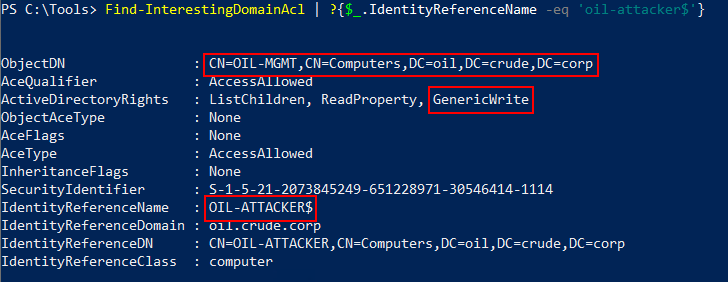
Hello All, In this post we will discuss on how to perform Resource-Based Constrained Delegation (RBCD) attack from an Linux machine to be specific we will use Kali Linux as an attacker machine. RBCD attacks is already been explained in detailed by Will Schroeder , Elad Shamir & Dirk-jan Mollema in their blog posts. What is Resource-Based Constrained Delegation (RBCD) ? In Windows Server 2012 Microsoft introduced a new type of delegation wherein the Service Administrators or Owner of the resources are allowed to configure which accounts are trusted to delegate to them. As per the Microsoft Docs this can also be configured across the domains. This also shifts the decision of whether a server should trust the source of a delegated identity from the delegating-from domain administrator to the resource owner. Access is controlled by the security descriptor on the target resource instead of an list of SPN records. The security descriptor are stored in msDS-AllowedToActOnBehalfOf