Walkthrough of Hackthebox DevOops system
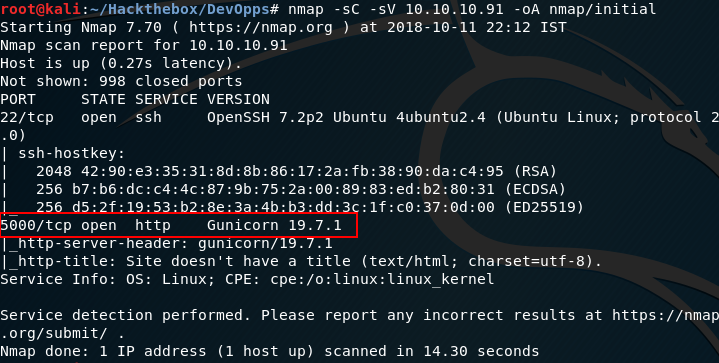
Hello Guys, it been a while since I have wrote a blog. Well without wasting any time lets dig into the devoops system of hackthebox as the title describes. Let fireup the namp on ip of devoops which is 10.10.10.91 and wait for port scan results. So we have 2 port open ssh(22) and http(5000) Lets check whats there on http as it may contain the door (vulnerabilities) which may allow us to get initial foothold. Hmm! Nothing interesting let fireup our favorite directory buster (gobuster). We Found 2 directory let view upload directory as the name looks very interesting. Well it seems the application allow us to upload xml file. Interestingly whenever I think of xml I always remember XXE attack. But in our case we need to craft the complete xml file with proper required elements. So we have crafted the xml with our payload to view the /etc/passwd file and boom 🎆 we got the passwd file. Now as we know that the XXE can be exploited so lets find some way to gain RCE o