Windows Red Team Lab Journey
Hello All,
It been long time since I wrote my last blog. Hopefully I will again get back on track and write some more blogs post soon which are in my to-do list. So without wasting more time lets focus on the Windows Red Team Lab Journey.
Introduction
The purpose of this post is to write the review about Windows Red Team Lab course which was hosted by Pentester Academy but now offered directly by Altered Security & designed by Nikhil Mittal. This course is all about performing Red Teaming assessment with assume breach mentality and capturing the flags. There are 3 options to opt for the labs 30 Days, 60 Days, 90 Days. You can choose any option depending on the time you will spend on the lab and prior knowledge about the red team like assessment. I opted for 90 Days lab as I knew I will only be able to spend time in night after office & my goal was to get all the flags from the lab.
What is Red Team ?
Red team is a independent group which challenges an organization to improve its effectiveness by adopting an adversarial approach. More or less the objective of red team is to evaluate detection, prevention & response capabilities of the organization.
What does Assume Breach means ?
Assume Breach is a mindset which limits the trust placed for application, services, identities and networks by treating them all (both internal & external) as not secure and probably already compromised. It means the organization accepts the fact that an attacker will succeed at any cost and then build the defenses accordingly.
Preparation before lab
After clearing the exam lot of my friends had asked me how did you prepared for this course. Before starting the course I had some background about the Active Directory based attacks. I had a small lab setup on my home machine for practice which consist of 1 AD(Win 2012), 2 Client (Win 10), 1 Kali Linux.
I mostly followed adsecurity.org & blog.harmj0y.net blog posts to practice various ad related attacks such as Silver Ticket, Golden Ticket, Ways of dumping ntds.dit, kerberosting etc. Before subscribing to the labs I had subscribed to Pentester Academy and watched Powershell for Pentesters & Abusing SQL Server Trusts in a Windows Domain as it was mentioned in the course outline. After subscribing for the Windows Red Team Lab course they provide video tutorials which are helpful during the course.
Altered Security also has a basic course Attacking and Defending Active Directory Lab which covers most of the active directory related attacks which can be used during Windows Red Team Lab course.
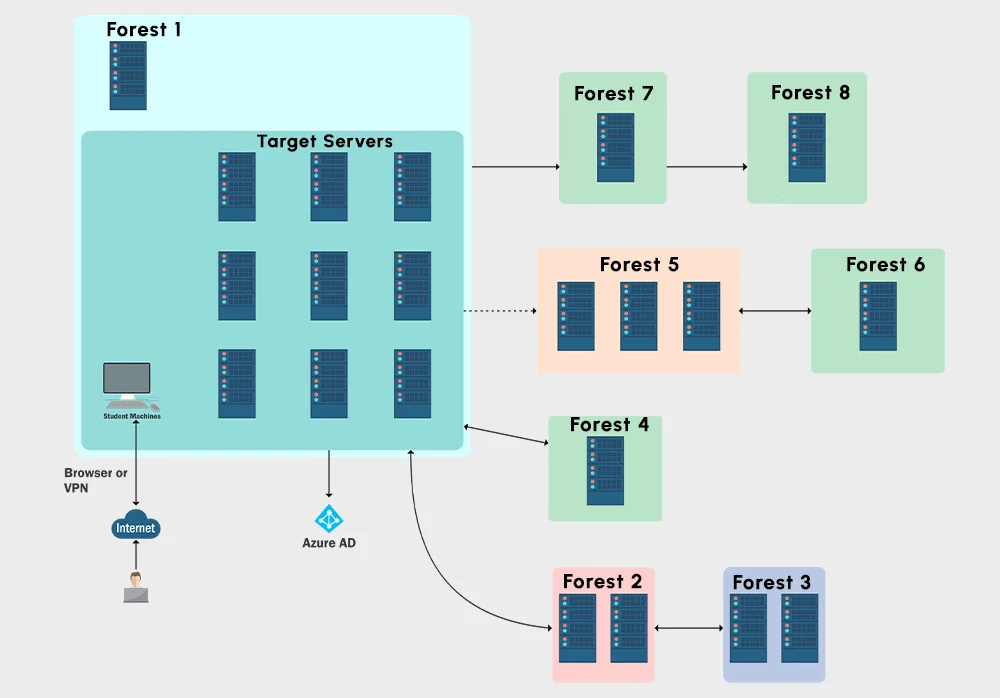
LAB Network
LAB Review
Students will be provided access to the student machine (Windows 10) with low privilege user in the Active Directory. The machine is connected to the Active Directory and has antivirus running. Students are tasked to escalate the privilege on the student machine to gain admin privilege and disable the antivirus to load the tools which will help them to progress in the lab. It is not possible to connect to the student machine apart from RDP.
Initially the lab is by default set with difficulty level as High but the student is given an choice to change it to normal. Student can only change the difficulty level twice in a month. I didn't change the difficulty level of the lab. I think that the challenging task always helps you to learn & explore more about the topic.
The lab helped me to learn many new things about Powershell, MSSQL, and Active Directory. This lab teaches how an enterprise can be compromised just via powershell and certain binary files. This lab is not about exploiting vulnerabilities, Its all about understanding misconfiguration & findings ways to compromise an enterprise network. I was able to capture all the flags in the lab.
I have mentioned the list of topic in the section Topics Covered in Lab which the student can learn while practicing in lab. I have also mentioned the list of tools & the reference links which I have used while doing the labs in the section List of Tools / Frameworks Used & Reference Links respectively.
Topics Covered in Lab
Note - The topic mentioned below are not in sequential order
It been long time since I wrote my last blog. Hopefully I will again get back on track and write some more blogs post soon which are in my to-do list. So without wasting more time lets focus on the Windows Red Team Lab Journey.
Introduction
The purpose of this post is to write the review about Windows Red Team Lab course which was hosted by Pentester Academy but now offered directly by Altered Security & designed by Nikhil Mittal. This course is all about performing Red Teaming assessment with assume breach mentality and capturing the flags. There are 3 options to opt for the labs 30 Days, 60 Days, 90 Days. You can choose any option depending on the time you will spend on the lab and prior knowledge about the red team like assessment. I opted for 90 Days lab as I knew I will only be able to spend time in night after office & my goal was to get all the flags from the lab.
What is Red Team ?
Red team is a independent group which challenges an organization to improve its effectiveness by adopting an adversarial approach. More or less the objective of red team is to evaluate detection, prevention & response capabilities of the organization.
What does Assume Breach means ?
Assume Breach is a mindset which limits the trust placed for application, services, identities and networks by treating them all (both internal & external) as not secure and probably already compromised. It means the organization accepts the fact that an attacker will succeed at any cost and then build the defenses accordingly.
Preparation before lab
After clearing the exam lot of my friends had asked me how did you prepared for this course. Before starting the course I had some background about the Active Directory based attacks. I had a small lab setup on my home machine for practice which consist of 1 AD(Win 2012), 2 Client (Win 10), 1 Kali Linux.
I mostly followed adsecurity.org & blog.harmj0y.net blog posts to practice various ad related attacks such as Silver Ticket, Golden Ticket, Ways of dumping ntds.dit, kerberosting etc. Before subscribing to the labs I had subscribed to Pentester Academy and watched Powershell for Pentesters & Abusing SQL Server Trusts in a Windows Domain as it was mentioned in the course outline. After subscribing for the Windows Red Team Lab course they provide video tutorials which are helpful during the course.
Altered Security also has a basic course Attacking and Defending Active Directory Lab which covers most of the active directory related attacks which can be used during Windows Red Team Lab course.
LAB Network
LAB Review
Students will be provided access to the student machine (Windows 10) with low privilege user in the Active Directory. The machine is connected to the Active Directory and has antivirus running. Students are tasked to escalate the privilege on the student machine to gain admin privilege and disable the antivirus to load the tools which will help them to progress in the lab. It is not possible to connect to the student machine apart from RDP.
Initially the lab is by default set with difficulty level as High but the student is given an choice to change it to normal. Student can only change the difficulty level twice in a month. I didn't change the difficulty level of the lab. I think that the challenging task always helps you to learn & explore more about the topic.
The lab helped me to learn many new things about Powershell, MSSQL, and Active Directory. This lab teaches how an enterprise can be compromised just via powershell and certain binary files. This lab is not about exploiting vulnerabilities, Its all about understanding misconfiguration & findings ways to compromise an enterprise network. I was able to capture all the flags in the lab.
I have mentioned the list of topic in the section Topics Covered in Lab which the student can learn while practicing in lab. I have also mentioned the list of tools & the reference links which I have used while doing the labs in the section List of Tools / Frameworks Used & Reference Links respectively.
Topics Covered in Lab
Note - The topic mentioned below are not in sequential order
- Local privilege escalation
- Domain enumeration
- Forest enumeration
- Command execution using MSSQL
- Escalating privilege from service account
- Credential replay
- Pass-the-hash
- Over-pass-the-hash
- Lateral movement
- Lateral movement using MSSQL
- Bruteforcing login
- Bypassing powershell constrained language mode
- Overcoming powershell remoting double hop issue
- Bypassing AMSI / Antivirus
- Kerberoasting
- Constrained delegation
- Unconstrained delegation
- Escalating privileges to enterprise admin
- Cross forest privilege escalation
- Social Engineering/ Phishing
- Impersonation
- Enumerating misconfigurations
- Enumerating for sensitive information
Exam Review
The exam is completely an practical exam. There are 8 systems in the exam with forest environment. Students are given 48 hrs to complete the exam, write the detail report & submit the report. The report should contain the step by step walk through to compromise the system. It should also contain the practical recommendation for all the misconfiguration which student has exploited to gain access on the system. The goal of the exam is to gain command execution on the system with any privilege.
I was able to compromise 7/8 systems in exam. I would like to say if you have completed the challenge lab the exam is easy otherwise you may find it bit difficult to solve.
Worth for Money
I would like to say yes the course is worth the money what you spend and what you learn. Weather you are a red teamer or pentester the lab has something for everyone to learn.
Note - This is completely my view about the course & the value for which it is being sold. You can agree or disagree on my views.
List of Tools / Frameworks Used
I was able to compromise 7/8 systems in exam. I would like to say if you have completed the challenge lab the exam is easy otherwise you may find it bit difficult to solve.
Worth for Money
I would like to say yes the course is worth the money what you spend and what you learn. Weather you are a red teamer or pentester the lab has something for everyone to learn.
Note - This is completely my view about the course & the value for which it is being sold. You can agree or disagree on my views.
List of Tools / Frameworks Used
- Nishang
- Powersploit
- Invoke-TheHash
- Inveigh
- Mimikatz
- Kekeo
- Rubeus
- PowerUpSQL
- Powercat
- Hashcat
- JohnTheRipper
- HeidiSQL
There are few more tools / frameworks which I have used during the lab & exam but I wont list down it here because it would directly reflect as answers to certain challenges which will be fun when you discover by yourself.
Reference Links
Below are few blog posts which I followed during the lab & exam.
- https://adsecurity.org/
- http://blog.harmj0y.net/
- http://www.labofapenetrationtester.com
- https://blog.stealthbits.com
- https://blog.netspi.com
- https://labs.mwrinfosecurity.com
Conclusion
Finally on the next day after 48 hrs of hard-work during exam I got the confirmation from Pentester Academy that I have cleared the exam. They also acknowledge over twitter.
I will suggest this course to everyone who want to challenge their knowledge about active directory/ red teaming.
Finally on the next day after 48 hrs of hard-work during exam I got the confirmation from Pentester Academy that I have cleared the exam. They also acknowledge over twitter.
I will suggest this course to everyone who want to challenge their knowledge about active directory/ red teaming.
Altered Security also issues the new certificate to their existing students. Students just need to send an email to the support team to get the certificate with new branding.
Thanks for reading the post.
Thanks to Nikhil Mittal for creating such a great Lab & Altered Security for hosting.
Special Thanks to all my friends who help / supported / motivated me for writing blogs. 🙏






Glad about it and it is surely a milestone to be achieved..You did it!!...Impressed by your dedication and passion to break things!!.congratz.
ReplyDeleteThanks :)
DeleteGrats! This is on my list. Want to be a little more knowledgeable academically though.
ReplyDeleteWorking with PK Medi Engineering was a smooth experience. Their team is highly professional and delivered the complete system on time, without compromising on quality. We will definitely continue working with them.
ReplyDeleteFor More Details: https://pkmec.com/